Security Minimalism, Part One: The Framework
Dec 2024Security is currently a complex collection of rules, regulations, niche solutions, fractured approaches, and the “moar!” effect: more vendors, more puzzle pieces that don’t really fit, more initiatives that don’t quite solve the basic, underlying problems, and more money being thrown at the problem without first stopping to look at how we ended up here.
Instead of jumping straight into complex controls, adding more vendors and their “solutions”, or trying to tick every box on a compliance checklist — often adding layers of security that don't actually solve anything — I’d argue that it's more effective to start small, focusing on fewer processes, simpler policies, and less complexity across the board. Focus on the essentials first, understanding how a lean and minimal security program can scale and how to leverage security as a force multiplier. Know when to handle security in-house, working on internal solutions that don’t add complexity, and when to bring in external solutions and the dependencies they create.
However, as Principle 2 states: “Security begins with people,” we need to start there, with how we work. How we approach security in a way that helps create and support security minimalism is our first stop.
In this three-part series, we'll explore how to implement security minimalism and how the right framework can help us stay focused on solving the most important problems. First then, a framework, built intentionally high-level and flexible, meant to be tailored to your specific program and organization. Once it's established and put into practice, security will gradually become more streamlined and remain minimal over time.
Note: I would like to acknowledge the tremendous value I gained by reading and learning from Phil Venables, General Jim Mattis, General Stanley McChrystal, Mark Mateski, and many others in the security world that are far too many to list here (you know who you are). I used what I've learned from them to create this framework.
The Framework
Start: Seek to Simplify Security (and Gain Cost Reduction)
As we saw in the Security Operating Model and Force Multiplying Security, effective security is simple, open, and automated. By simplifying and automating security we can focus on providing the right guardrails needed to keep the business running in a safe way, and by being open and transparent in our practices and communication, we begin the process of force multiplication, teaching security and trusting the teams to have the business needs and security in their minds as they design the next products.
To support this, we need to focus on the key actions that will help us keep security solutions minimal and cost-effective. Here are the main focus areas to start with:
- Prioritize the issues based on risk—address the most critical problems first.
- Use what you have and utilize the configuration of existing software, solutions, or systems to enhance security and reduce risk.
- Then automate and self serve security processes and solutions to integrate security seamlessly into operations.
- Introduce additional software, solutions, or products only as a last resort or when mandated by compliance requirements.
Work Focus
There are some fundamentals that need to happen first and foremost. These basics should lead all efforts in this more minimalist security program, and they are:
- Systemic risk mitigation
- Defense in depth
- Data and identity protection
- Incident response and a plan to go with it
- Proactive security and intelligence gathering
Leadership Approach
It all starts with leadership—at every level of the security organization and beyond.
All leaders in the security organization are expected to own their areas of responsibilities and are required to be independent in thinking, making decisions, and providing their teams with the direction and information they require to be successful.
For a security program to work, and in general, the leadership should take the following approach:
- Intent is clear: Clear communication of the strategic intent to empower everyone’s decision-making. The more you understand the intent, the better you can make decisions quickly, knowing the main goal of what we need to accomplish.
- Small team: “Minimal Staff, Maximum Trust”. Small, nimble teams can move more fluidly.
- Delegation is key: Delegation down the chain fosters autonomy among each member of the team, building the muscle memory that will enable rapid decision making.
- Freedom to work with others and create relationships: Build a Liaison/Champion program and a Team of Teams, where we can enable others to help us by teaching them security.
In general, leaders will work to always push forward and be dynamic. Each leader will:
- Think strategically.
- Secure holistically.
- Take swift action.
- Constantly work to make things better.
Leaders are ultimately responsible for all that happens in their teams. They identify the problem, recognize the impact, take ownership, and solve it. This should be their framework.
Rather than looking for excuses, figure out what the problem is, realize how you’re contributing to it, and fix it. That’s how problems get solved—by consistently applying the framework, no matter how difficult it is.
Automation
A small team, in support of security minimalism, can make a big impact by taking advantage of automated processes and a self-service approach to security. This frees the teams to tackle the more challenging security issues, focusing on not creating complexity.
In general:
- Use automation to gain an advantage in actions such as threat detection and initial incident response, managing permissions, and making other critical security decisions quickly and effectively.
- Build platforms and frameworks to help other teams and departments, reducing the need for more vendors, solutions, or software.
But be ready to reimplement if it doesn’t optimize work. It's all about contantly looping and assessing whether the solution is working.
Using Guardrails, Lowering Risk and Building Resiliency
It all starts by understanding the values of each service, solution, and system in the organization. Focus on understanding criticality and importance. The more critical they are the less flexible security should be, with tighter policies and controls.
Develop a framework for "Open Guardrails", enabling individuals to contribute improved guardrails by creating plugins or integrating their own solutions to help secure the company, thus making it more secure and resilient. However, expect incidents.
But remember: not all incidents are equal. Understand the effects of incidents and what can go wrong after that. Factor in second order effects. This is why it is extremely important to have a clear incident response plan and team, and constantly test the assumptions.
Resilience and Business Continuity
- Build a resilience testing program rather than a business continuity one. This must include evaluating the ability of systems, applications, processes, or organizations to withstand and recover from security incidents and breaches, adverse conditions such as degraded performance due to a security vulnerability, disruptions, or failures.
- Constantly test and break security. Using internal and external people, test our ability to detect and react to security issues. Understand what would happen if something breaks completely.
- Build the Business Continuity by forcing the day to day policies and processes to be “hardcore resilient”. Adopt a security-by-design and risk-based approach, focusing in risk prioritization and mitigation in all our processes and services, and create redundancies whenever possible.
- Develop a strategy for unforeseen scenarios. Create contingency plans for potential and unknown security threats. Use creative thinking to anticipate what could compromise the company’s security, identify potential threat actors, and assess whether existing controls can be deployed to reduce the likelihood or impact of such events.
- Do not forget the “low provability high consequence” risks. Pay special attention to these, when they occur, it’s often very bad.
- Always bias "de facto" over "de jure"
- Find and value your Champions. Use them to help lower risk.
Measuring and Documenting
Equally important, if not more so, is understanding how things are progressing. We must establish effective ways to track and document our efforts, enabling us to assess quickly when adjustments are needed. In general:
- Measure “adoption", not just "compliance".
- Institute an active risk governance process to define your risk appetite / thresholds.
- Document risks in a risk register.
- Create escalation/decision processes and monitor those.
- Create reporting frameworks and dashboards, enabling a transparent risk posture for internal and external stakeholders.
How Does This Work?
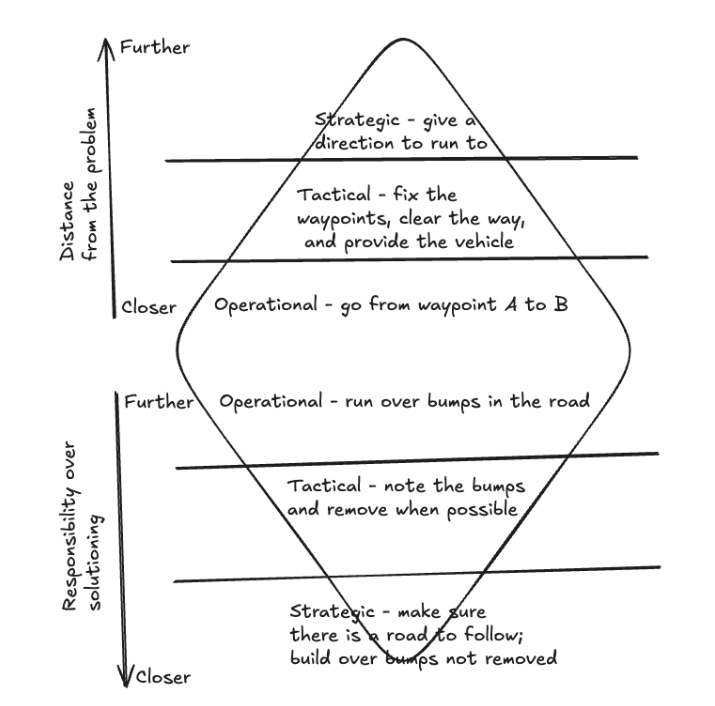
Image by Izar Tarandach
The strategic level is at the "top leadership", where the overall direction is set and the responsibility lies in removing obstacles that hinder progress toward the solution.
The tactical level is "middle leadership", focused on creating roadmaps to move from the current state to the desired outcome. It’s about mapping the path, clearing obstacles, and bridging the gap between strategic goals and operational execution. This level is responsible for identifying and removing barriers to progress.
The operational level is where the work gets done by the "doers" in the team. It focuses on implementing solutions based on the strategy and roadmap, reporting obstacles along the way, so the other levels can respond quickly. It is the level that is closest to the bits and bytes of getting the solution working, but at the same time it is the level that is further from the responsibility for solutioning - once the strategy of what to do and the tactic of how to do it are set, they carry the responsibility for the solution coming up, via management of the operational level.
The Strategic Level
This level carries the biggest responsibilities - for identifying what’s next and for enabling the solutions. The direction is spelled out in the Security Strategy document or something similar, that sets the road and the direction to follow. It is the furthest from “how to solve” and the closest to “I am responsible for the solution”.
This level is responsible for prioritizing identified risks and solutions, securing the necessary resources, and communicating the outcomes—whether successful or not—to leadership. Additionally, it focuses on developing the tactical and operational teams, ensuring they have everything they need to execute effectively.
The Tactical Level
This is likely the most challenging level, as it sits between responsibility and execution. It requires independence and initiative, while also the ability to step back from daily problem-solving and avoid rehashing strategic decisions.
Following the guidance above (leaders will work to always push forward and be dynamic), this level will mainly act decisively and advance endlessly. This translates to solving as many issues as possible (“removing the bumps”) so that they do not stop the operational work and do not clog the strategic work. There is huge responsibility in doing both, and it needs to be clear that mistakes will happen- but mistakes are a learning opportunity, and a way to advance endlessly. It is not a matter of one step forward two steps back - it is a matter of acting decisively to go to the next objective, and experiencing any possible and expected mistake as a learning opportunity to advance better next time.
This level also carries the biggest amount of delegation responsibility - it gets to give responsibility to the operational level, and it gets to share responsibility with the strategic level. The way this happens is by realizing that one cannot do everything and be everywhere in a situation where we are trying to have minimal staff, maximum trust - the trust needs to be given so that the minimal staff can work in an agile way. Again, mistakes will happen and that is part of the way. The way the mistake is used as a learning experience is more important than the mistake happening.
When delegating, giving full trust means the delegation is complete, but accountability remains. Trust should be based on past performance — those who handle it well will be trusted with more. If someone struggles, they’ll be supported and learn from challenges, with trust adjusted accordingly but always aiming to grow. People are empowered to succeed when this level understands that growth happens over time.
This level is also the best positioned to translate the risk identified by the operational level into attention-focus items that the strategic level needs in order to secure holistically. What this means is that the strategic level needs to be less bogged by “this particular firewall rule is bad” or “this particular package/service/vendor has risk” and more informed by “if we keep these risks we have identified in place, the business is at risk of such and such impact”. This enables the strategic level to go up to leadership and request the resources and changes that are needed. This translation goes both ways: the tactical level is responsible for taking the strategy and using the language of risk to translate to the operational level “this is why thing A needs to happen before thing B”, and “this is why we need to do thing C this way and not the other way”.
In the roads and waypoints analogy, this level acts very much as the traffic warden, making sure that crossings are always open and the traffic is flowing. The way that gets done is by translating between strategy and operational levels and making sure everyone has the fuel they need to keep the trucks moving.
The Operational Level
Ultimately, someone needs to take action. The operational level is closest to both identifying the problem and executing the solution. Often, this level is the one to propose the initial solution.
This level relates to the framework by way of securing holistically and advancing endlessly. The most important characteristic of this level is psychological safety - the tactical and strategic level must provide an environment where this level can operate with the freedom to try different solutions and point at different risks and learn along the way.
The most important responsibility for this level is to keep the tactical and strategic levels informed, with time being of essence. As soon as a bump on the road is identified as one that can’t be solved at the operational level, it must be floated up to tactical and strategic so it can be dealt with the tools they have at their disposal.
Using the "Work Focus" part of the framework, this level has the widest visibility to identify what needs to be fixed, and how it impacts the business. Their responsibility is to take these items and using the language of risk, work with strategic and tactical levels on when to solve and which tools to use as solutions.
Due to their proximity to the issues, this level is uniquely positioned to identify automation opportunities. Automating processes has to be seen as at least 30% of this level’s focus, since it works towards minimal staff, maximum trust by creating processes that can be tweaked until they free staff effort to concentrate on the next important thing, with maximum trust that the results are appropriate to the margin of error that the strategic and tactical levels are ready to accept. In this sense, automation at this level takes central part in securing holistically (aiming to create automated processes that cover the greatest number of cases) and at the same time identifying bumps on the road to automation (for example, legacy cases that stop the automation from working or that present edge cases that need to be addressed differently). These cases then get passed to the tactical level so the bumps can be removed.
Process automation doesn’t mean everything is a simple shell script. Being close to the issues, this level identifies repeatable business processes that can be "automated" with guardrails in place. It works closely with the operational teams across other departments, building inter-team relationships and creating liaisons. This collaboration helps ensure guardrails are effective and aligned with other teams, and often leads to identifying tasks that can be delegated to other teams for further definition and execution.
Another important responsibility is that people working at this level are best positioned to measure adoption versus compliance. By having these inter-team relationships the operational level is able to actually see how adoption is working or not. Again, this is to be considered as a bump in the road that tactical and strategic will need to clear. The important thing here is to recognize the patterns that are stopping adoption and solve for those.
This level is at the highest risk of burnout, so it’s crucial to know when to step back and ask for help, with tactical and strategic levels offering support. It’s also key to identify Champions and Partners who can reduce context switching and help operational staff grow. This level fosters curiosity, ensures information flows, and helps elevate staff to a more tactical mindset, multiplying impact. By building relationships and creating frameworks, this level uses trust and leadership to maximize results with minimal resources.
To Close
Security is a force multiplier, and as such there is a real need to focus on having the right people and the right processes. Then, and only then, we can focus on the right tools - tools that help us keep security simple and minimal.
Only by identifying the simplest effective security baseline, sharing it for others to use, and continuously reducing, automating, and simplifying, can we keep security minimal.
